

How Do You Know if You Have the Right Security Policies and Capabilities in Place?
History has proven traditional cybersecurity does not work. Aligning to a Zero Trust framework is the solution to protecting your organization and critical data from adversarial threats, but how do you know your policies and capabilities are adequate and correctly configure to achieve the desired outcomes? A Zero Trust assessment with ZTROAM moves your networks to the left of breach.
Zero Trust Compliance In Three Easy Steps.
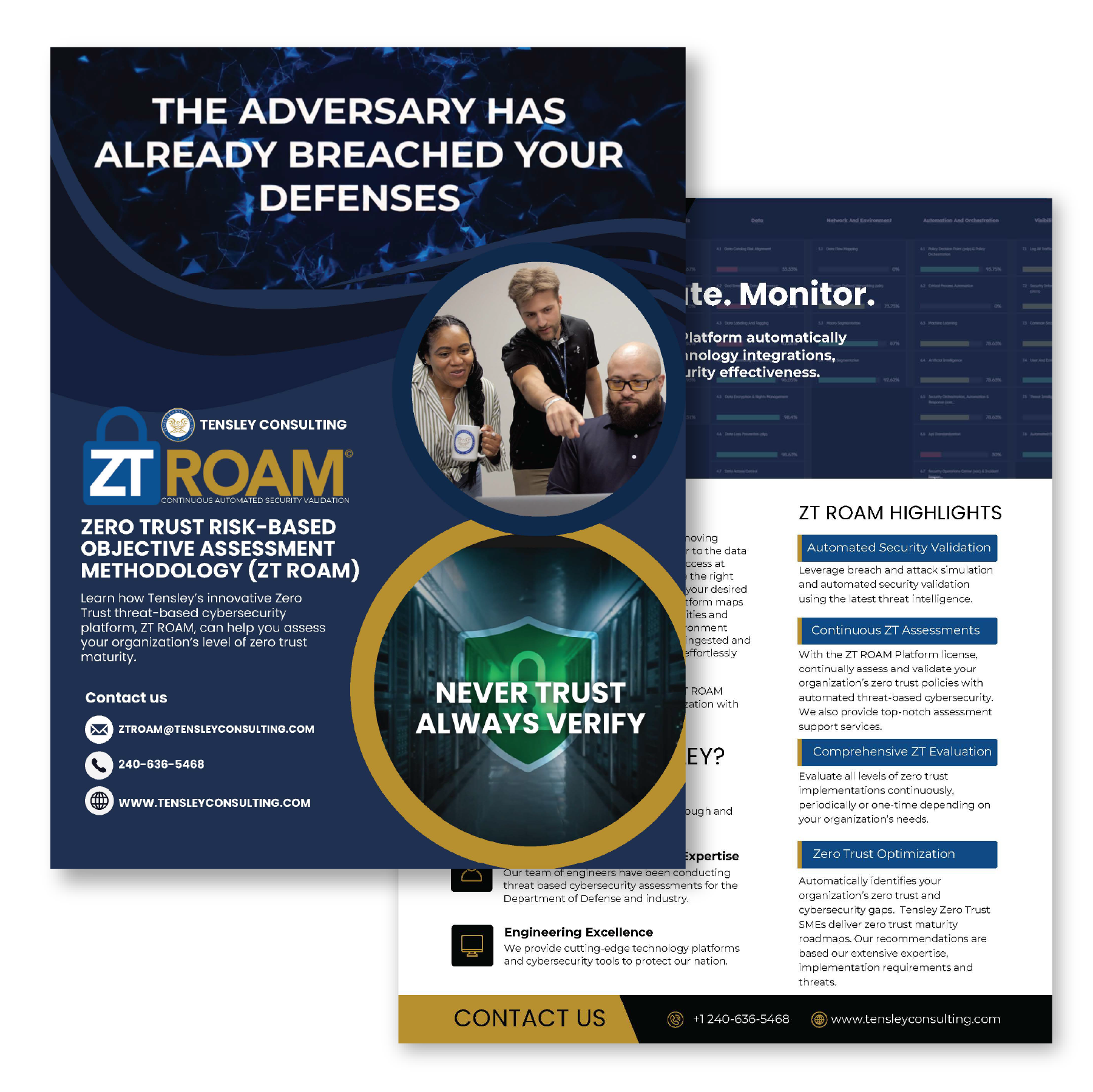
Assess. Validate. Monitor.
Assess
Our Zero Trust assessment tool leverages breach and attack simulation and automated security validation to assess your organization’s level of zero trust maturity and the effectiveness of implemented cybersecurity capabilities and controls.
Validate
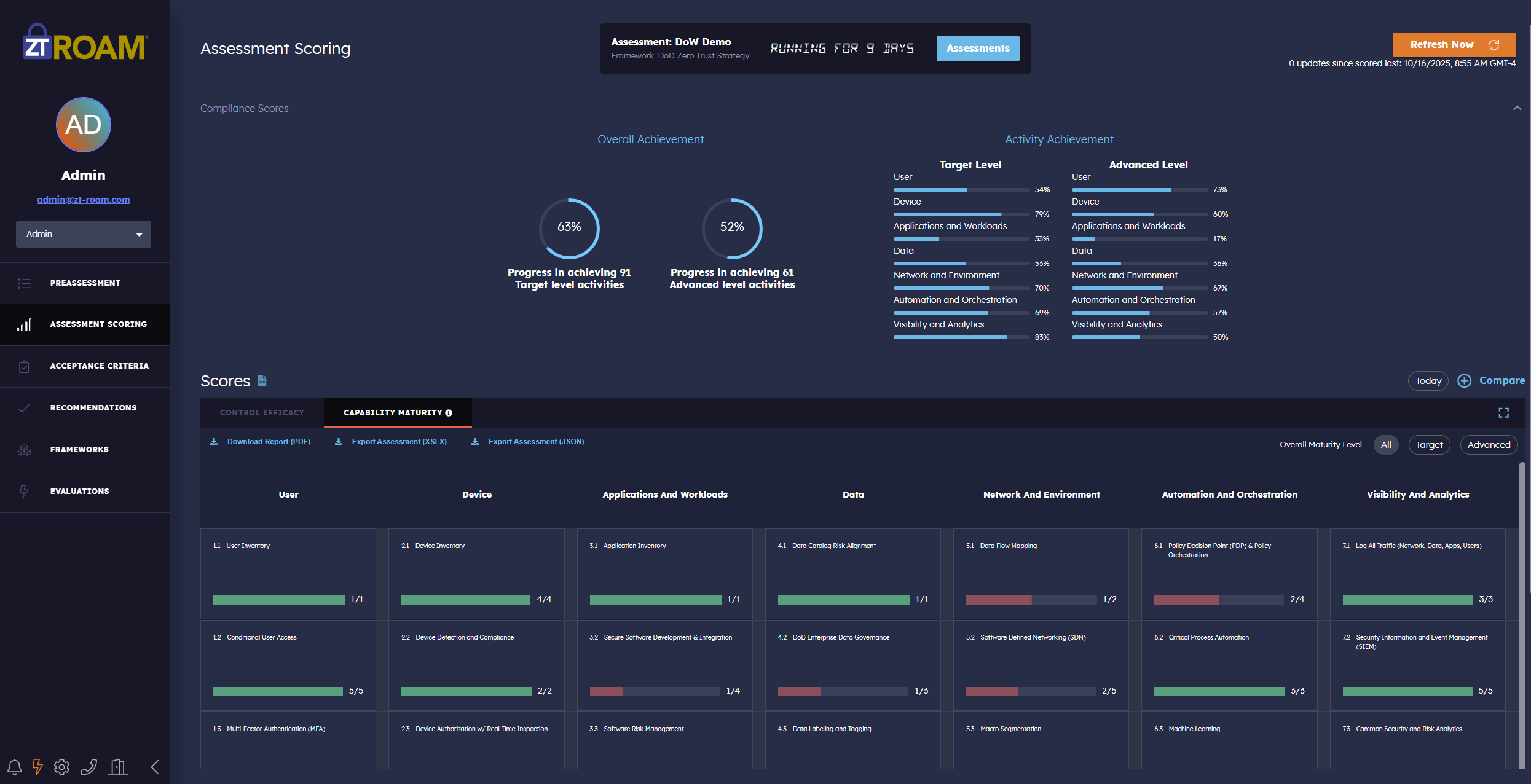
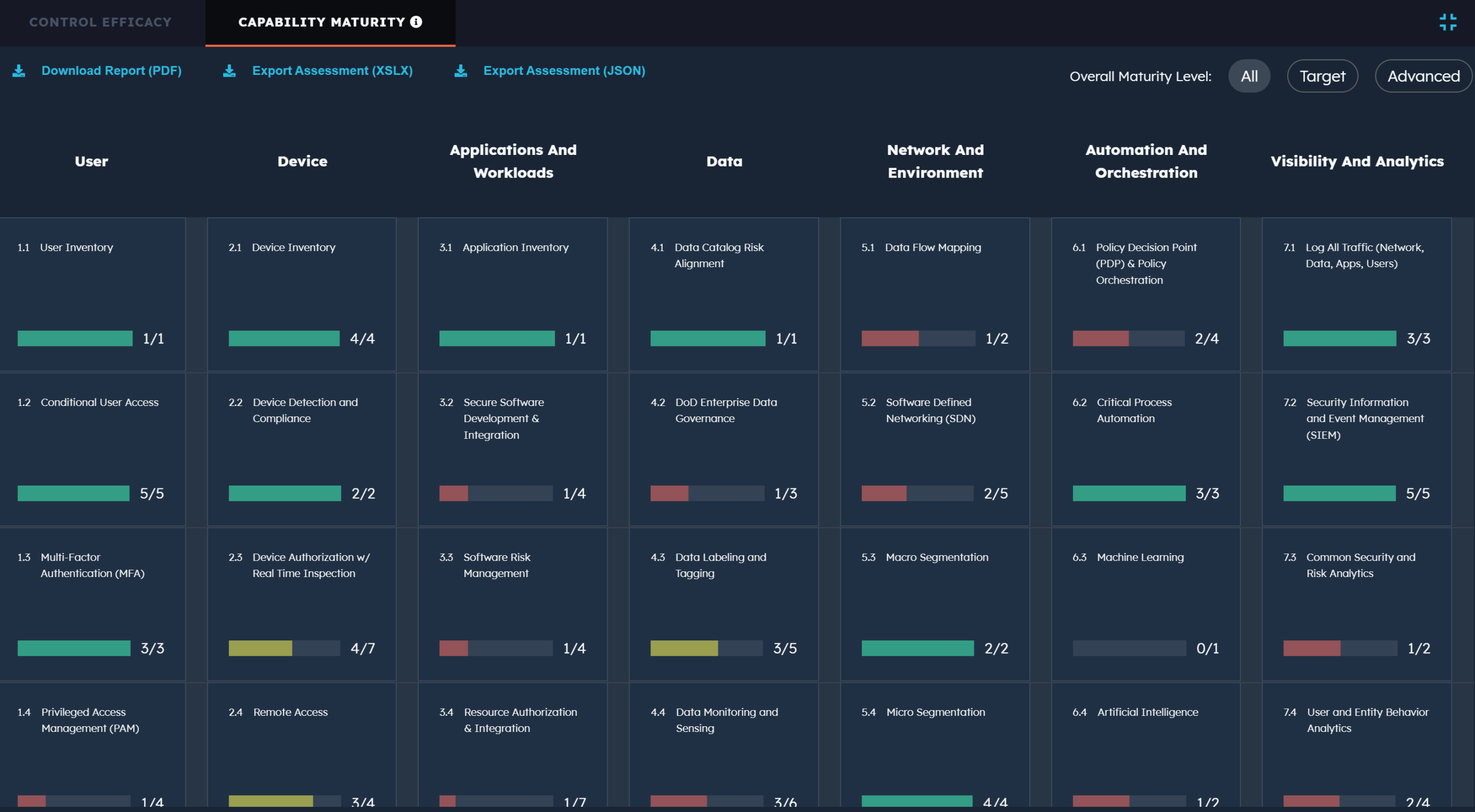
Our Zero Trust assessment tool validates and visually depicts which zero trust capabilities and activities have been achieved across government and industry frameworks. Your organization’s zero trust capabilities and policies are validated based on our innovative zero trust threat-based assessment methodology.
Monitor
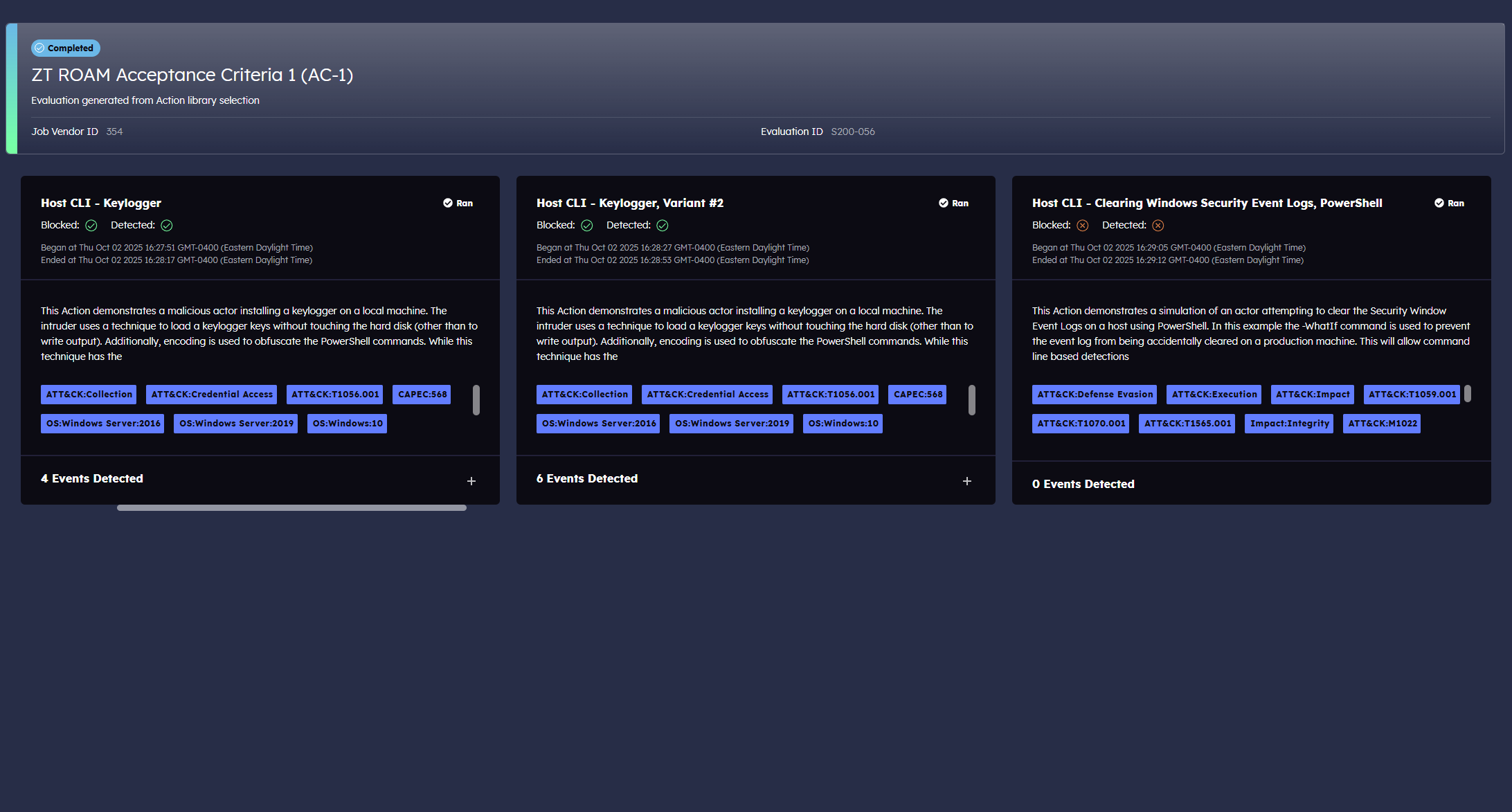
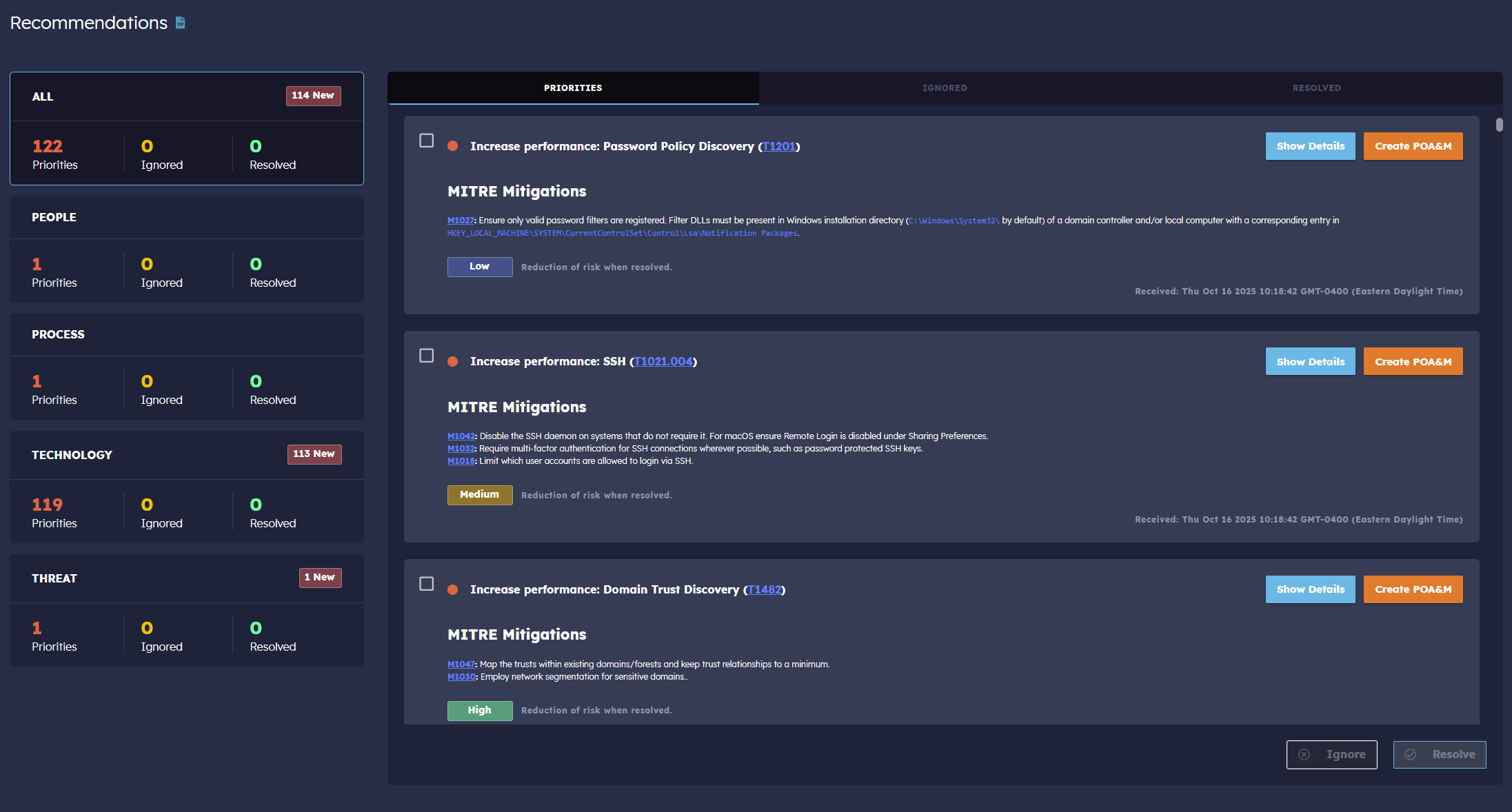
Monitor the progress of your Zero Trust transition with our comparison tools and targeted recommendations. Create plans of action and bring your environment into E.O. 14028 Zero Trust compliance.
ZT ROAM Elevates Your Organization’s Cybersecurity
Automated Security Validation
Leverage Breach and attack simulation and automated security validation with latest intelligence. Mapped to the MITRE ATT&CK adversary lifecycle framework.
Continuous Zero Trust Assessments
Continually assess and validate zero trust policies with automated threat-based cybersecurity.
Flexible Zero Trust Assessments
Evaluate your organization’s level of zero trust maturity and cybersecurity based on your needs, such as one-time, quarterly or annually.
Zero Trust Optimization
Automatically identifies zero trust gaps to support delivering zero trust maturity recommendations.
Your Guide to ZT ROAM
Discover how the ZT ROAM Integrated Platform can transform your operations with cutting-edge technology and seamless connectivity. Our comprehensive overview provides insights into the features, benefits, and real-world applications of our platform. Fill out the form to download your copy and take the first step toward optimizing your integrated solutions.
Download Our Overview Sheet
Our ZT ROAM Integrated Platform Overview will be delivered right to your email!

Frequently Asked Questions
Transparency matters. Review our FAQs to learn more about ZT Roam’s features, requirements, and policies.
What is ZT ROAM?
Tensley’s ZT ROAM Platform, developed with our innovative zero trust assessment methodology, empowers your organization with real-time, automated zero trust assessments.
Why Zero Trust?
Organizations move to Zero Trust because it dramatically reduces breach risk, protects modern hybrid work environments, and ensures only verified users and devices can access sensitive resources. It replaces outdated perimeter‑based security with continuous verification, making it far harder for attackers to move laterally or exploit implicit trust.
Can ZT ROAM export assessment results?
Yes, executive summaries, assessment results, and recommendations can be exported in three formats: PDF, XSLX, and JSON.
What is the cost of a license for ZT ROAM?
An annual license of ZT ROAM is valued at $50K. This allows the customer to assess one environment regardless of size. If customers need to assess multiple environments, bulk licensing and multi-year discounts are available.
Where can I download the software?
Licensing and software are available on our ZT ROAM download portal.
Does ZT ROAM or Tensley keep my data?
No, you are in complete control of software user access as well as the assessment data. We are an agentless platform.
Is ZT ROAM training available?
Yes, training and professional services are available for users of ZT ROAM.
Can I perform manual assessments with ZT ROAM?
Yes, stand-alone environments and tactical systems can still be assessed using the manual scoring capabilities within ZT ROAM.
What are the ZT ROAM OS requirements?
RHEL 9 or Rocky Linux 9
Docker – v20.10.22+
Docker-compose – v2.14.1+
What are the ZT ROAM hardware requirements?
Processor – 64-bit x86 CPU with at least 4 cores
Memory – 16GB
Disk Storage – 200GB
Disk Type – 10k SAS+
Network – Single network interface; Static Routable IP addresses required
What are the ZT ROAM Network Requirements?
ZTROAM needs permissions to create and run Docker containers via Docker Compose.
Port 443: Inbound / ZT ROAM UI
Port 8089: Outbound / SIEM (Optional)
Port 443: Outbound / BAS or Security Tool (Optional)
Is ZT ROAM’s data encrypted?
Passwords and Data at Rest are encrypted within ZT ROAM.
Zero Trust Risk-Based Objective Assessment Methodology (ZT ROAM)
Tensley’s ZT ROAM Platform, developed with our innovative zero trust assessment methodology, empowers your organization with real-time, automated zero trust assessments. Our team has extensive expertise in zero trust and threat-based cybersecurity assessments.
Who Can Benefit from ZT ROAM?
ZT ROAM’s Integrated Platform is designed to empower a diverse range of industries and professionals. Whether you’re in transportation, logistics, or technology, discover how our innovative solutions can streamline your operations, enhance connectivity, and drive success. Explore the possibilities and see how ZT ROAM can be a game-changer for your business.

Tensley Heads to the 15th Annual Billington Cybersecurity Summit – Join Us There!
Tensley Consulting is excited to participate in the 15th Annual Billington Cybersecurity Summit in Washington D.C., showcasing their innovative zero trust platform, ZT ROAM, and engaging with industry leaders on cybersecurity advancements in the AI age.

Zero-Trust Tech Talk
Tensley Consulting hosted its inaugural Tech Talk in May, focusing on the practical applications of Zero Trust, where experts provided an interactive and informative session with resources for ongoing learning, marking the beginning of a new series of educational events.
